Cross-Site Request Forgery - CSRF
You visit a malicious site which has an image like this
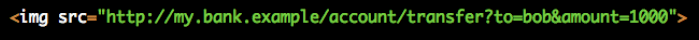
Learn Ruby on Rails - Ruby on Rails tutorial - Cross-Site Request Forgery - CSRF - Ruby on Rails examples - Ruby On Rails programs
Only accepting POST does not really help
By default Rails 2.0 will check all POST requests for a session token
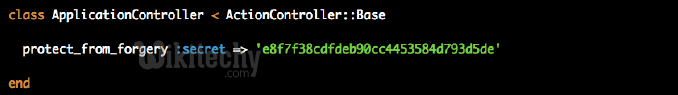
Learn Ruby on Rails - Ruby on Rails tutorial - Cross-Site Request Forgery - CSRF - Ruby on Rails examples - Ruby On Rails programs
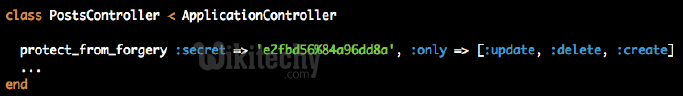
Learn Ruby on Rails - Ruby on Rails tutorial - Cross-Site Request Forgery - CSRF - Ruby on Rails examples - Ruby On Rails programs
All forms generated by Rails will supply this token
CSRF Protection in Rails
- Very useful and on-by-default, but make sure that
- GET requests are safe and idempotent
- Session cookies are not persistent (expires-at)
SQL Injection
- The users input is not correctly escaped before using it in SQL statements

Learn Ruby on Rails - Ruby on Rails tutorial - sql injection - Ruby on Rails examples - Ruby On Rails programs

Learn Ruby on Rails - Ruby on Rails tutorial - sql injection - Ruby on Rails examples - Ruby On Rails programs
SQL Injection Protection in Rails
Always use the escaped form
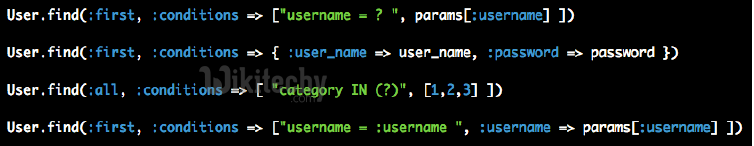
Learn Ruby on Rails - Ruby on Rails tutorial - sql injection - Ruby on Rails examples - Ruby On Rails programs
If you have to manually use a user-submitted value, use `quote()`
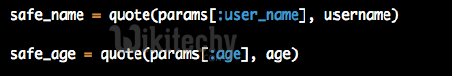
Learn Ruby on Rails - Ruby on Rails tutorial - sql injection - Ruby on Rails examples - Ruby On Rails programs
JavaScript Hijacking
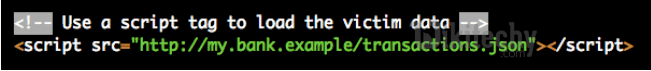
Learn Ruby on Rails - Ruby on Rails tutorial - Javascript hijacking - Ruby on Rails examples - Ruby On Rails programs
JSON response

Learn Ruby on Rails - Ruby on Rails tutorial - Json response - Ruby on Rails examples - Ruby On Rails programs
- The JSON response will be evaled by the Browser’s JavaScript engine.
- With a redefined `Array()` function this data can be sent back to http://my.evil.site
JavaScript Hijacking Prevention
- Don’t put important data in JSON responses
- Use unguessable URLs
- Use a Browser that does not support the redefinition of Array & co,
- currently only FireFox 3.0
- Don’t return a straight JSON response, prefix it with garbage:
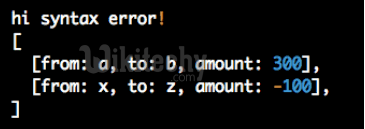
Learn Ruby on Rails - Ruby on Rails tutorial - Hijacking Prevention - Ruby on Rails examples - Ruby On Rails programs
The Rails JavaScript helpers don’t support prefixed JSON responses
Mass Assignment
User model
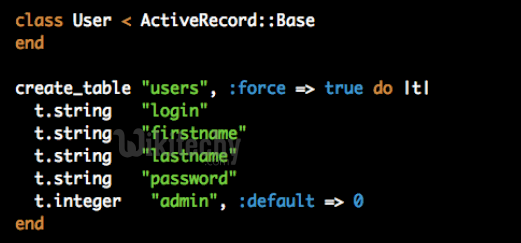
Learn Ruby on Rails - Ruby on Rails tutorial - mass assignment - Ruby on Rails examples - Ruby On Rails programs
Handling in Controller
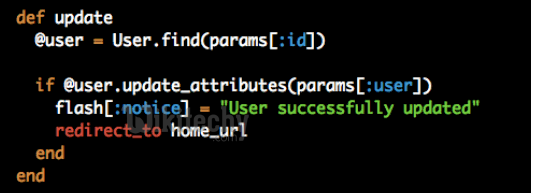
Learn Ruby on Rails - Ruby on Rails tutorial - Handling controller - Ruby on Rails examples - Ruby On Rails programs
A malicious user could just submit any value he wants

Learn Ruby on Rails - Ruby on Rails tutorial - Handling controller - Ruby on Rails examples - Ruby On Rails programs
Use `attr_protected` and `attr_accessible`
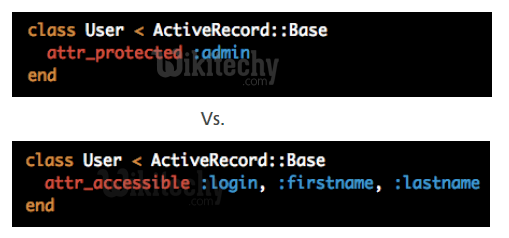
Learn Ruby on Rails - Ruby on Rails tutorial - attr protected vsattr accessible - Ruby on Rails examples - Ruby On Rails programs
Start with `attr_protected` and migrate to `attr_accessible` because of the different default policies for new attributes.
