hacking tutorials - what is a computer virus - hacker - ethical hacking - learn hacking - ethical hacking tutorials
- A potentially damaging computer program capable of reproducing itself causing great harm to files or other programs without permission or knowledge of the user.
- Computer viruses are perceived as a threat to both business and personnel
- Virus is a self-replicating program that produces its own code by attaching copies of itself into other executable codes
- Operates without the knowledge or desire of the computer user
Learn ethical-hacking - ethical-hacking tutorial - what-is-a-computer-virus - ethical-hacking examples - ethical-hacking programs
- Computer viruses are a type of software program that, like a biological virus, reproduces and spreads itself
- Some virus may display only a message on the screen, others may slow down the Pc
- They can also erase files or even format your floppy or hard disk and crash the system.
Learn ethical-hacking - ethical-hacking tutorial - computer-virus - ethical-hacking examples - ethical-hacking programs
Who creates/writes viruses ?
- Gather information about the destination or host. This provides huge money for the attackers by gathering the information like bank details or any other confidential informations.
- Virus/Antivirus market - It’s a high end potential business in the field of antivirus. Many antivirus companies are making billions of money in this field or removing virus.
PSYCHO CASES
- For Fun - To make fun on others, hackers will attack the victims.
- To Take Revenge on others
- To show Anger by attacking the victims / opponents

Learn ethical-hacking - ethical-hacking tutorial - virus - ethical-hacking examples - ethical-hacking programs
Characteristics of a Virus
- The virus will resides in the memory and replicates itself while the program where it attached, is running May or May not - Does not reside in the memory after the execution of program Can transform themselves by changing codes to appear different Hides itself from detection by three ways:
- Encrypted Viruses - Encrypts itself into cryptic symbols
- Memory consuming virus - Alters the disk directory data to compensate the additional virus bytes
- Corrupt disk data - Uses stealth algorithms to redirect disk data
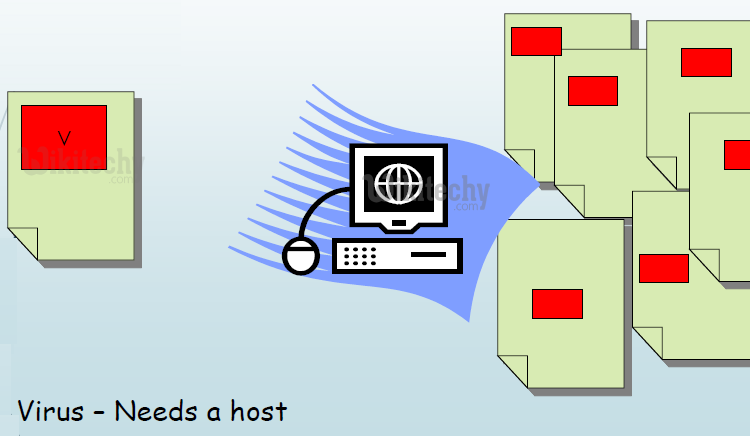
The functional logic of a Virus
- Search for a file to infect.
- Open the file to see if it is infected.
- If infected, search for another file.
- Else, infect the file.
- Return control to the host program.
Learn ethical-hacking - ethical-hacking tutorial - program-virus - ethical-hacking examples - ethical-hacking programs
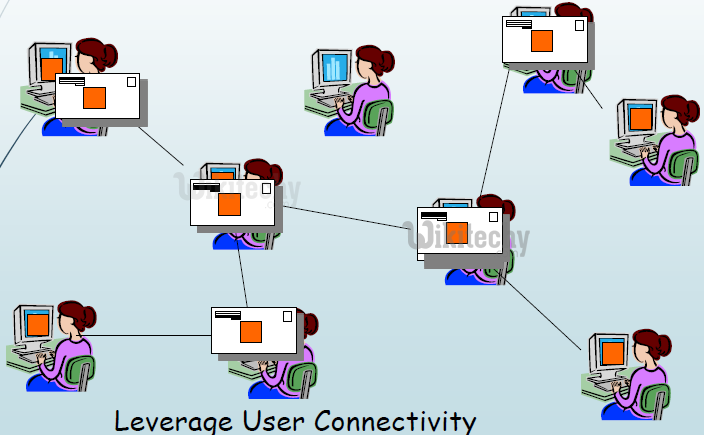
Virus Propagation
Learn ethical-hacking - ethical-hacking tutorial - virus-propogation - ethical-hacking examples - ethical-hacking programs
Prevention & cure of computer viruses
- Install an Antivirus software
- Regularly update the program
- Open email attachment files only if you are expecting the attached files, or the sender is known and has confirmed sending the file
- Try to avoid downloading and installing software from the Internet
- Install only registered copies of software on the system
Removal of Some Common Viruses
- We can remove some of the common viruses without help of any antivirus Program.
- e.g.- New Folder.exe, Autorun.inf
New Folder.exe
- It looks just like an folder but actually it is a .exe file.
- Try to deleting the file.
- It will delete if you haven’t executed it, if you’re unable to delete it.
- Go to Task manager ( by pressing ctrl+shift+del )
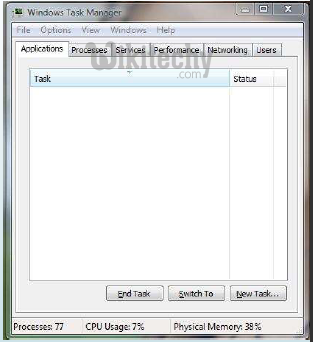
Learn ethical-hacking - ethical-hacking tutorial - task-manager - ethical-hacking examples - ethical-hacking programs
- Go to Process Tab and try finding that the process for
- the exe file and end the process.
- Then Go to the same folder containing the exe file and
- delete it.
- Then Open Search and try finding the .exe files of same
- size and delete them all.
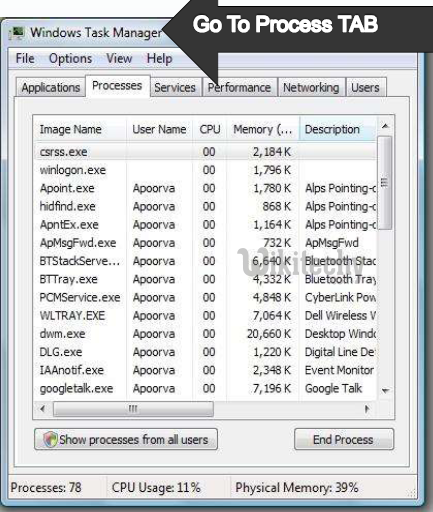
Learn ethical-hacking - ethical-hacking tutorial - task-manager-process-tab - ethical-hacking examples - ethical-hacking programs
Removal of Autorun.inf
- Open Run dialog Box. Type in “CMD” press ENTER.
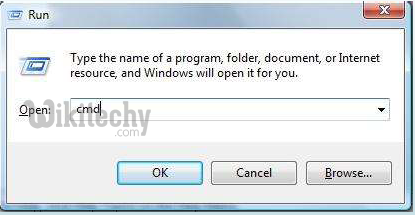
Learn ethical-hacking - ethical-hacking tutorial - run-command - ethical-hacking examples - ethical-hacking programs
- The Command Prompt will Open Now. In Command prompt go to the drive containing Autorun.inf
- Now Type In “ attrib -h -s -a” and press enter
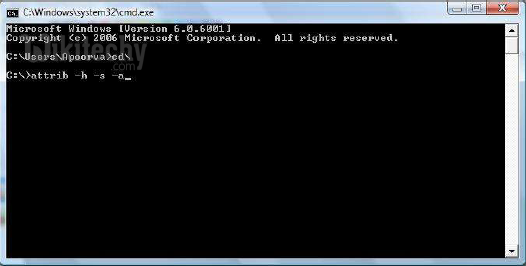
Learn ethical-hacking - ethical-hacking tutorial - attrib-command - ethical-hacking examples - ethical-hacking programs
- This will remove drives attributes for all Hidden, System files.
- Now Type “ Del autorun.inf” and press ENTER.
- The Virus has been Successfully Removed
