Client Side Attacks - Types of Client Side Attacks - Cyber Security Tutorial
Types of Cyber Attacks
Client Side Attacks
- A client-side attack is a security breach that happens on the client side.
- Examples include installing malware on your device or banking credentials being stolen by third-party sites.
- For example, if you tried to log into your bank’s website using an out-of-date browser and plugin, you would be denied access.
- Another common client-side attack is data manipulation, for example, changing your bank balance without your permission.
- On the other hand, a security breach on the client side should be prevented by using positive client-side security measures such as multifactor authentication and encryption.
- Ideally, computers should only be connected to trusted networks and devices with proper security patches installed.
- Client-side attacks are harder to prevent since they require access to your device, but can be mitigated by taking appropriate steps beforehand.
Types of Client-Side Attacks
Content Spoofing
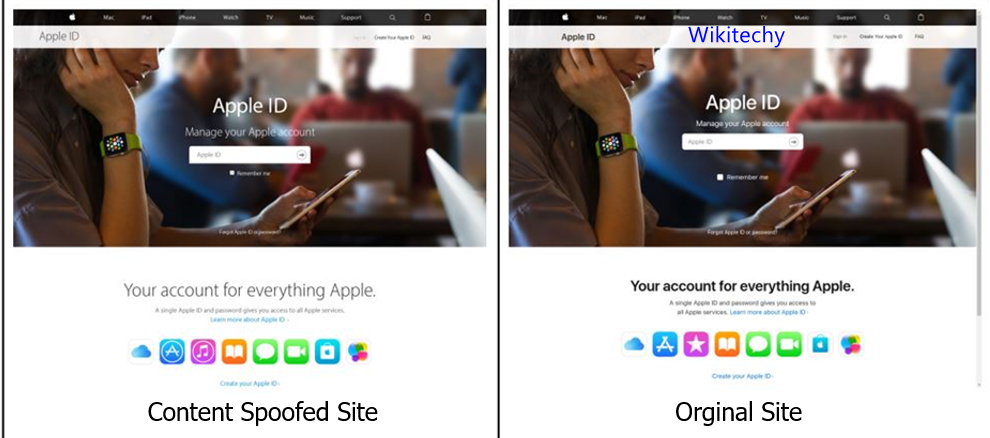
- Content Spoofing is one of the common web security vulnerabilities.
- It allows the end user of the vulnerable web application to spoof or modify the actual content on the web page.
- The user might use the security loopholes on the website to inject the content that he/she wishes into the target website.
- When an application does not properly handle user-supplied data, an attacker can supply content to a web application, typically via a parameter value, that is reflected back to the user.
Cross-site scripting
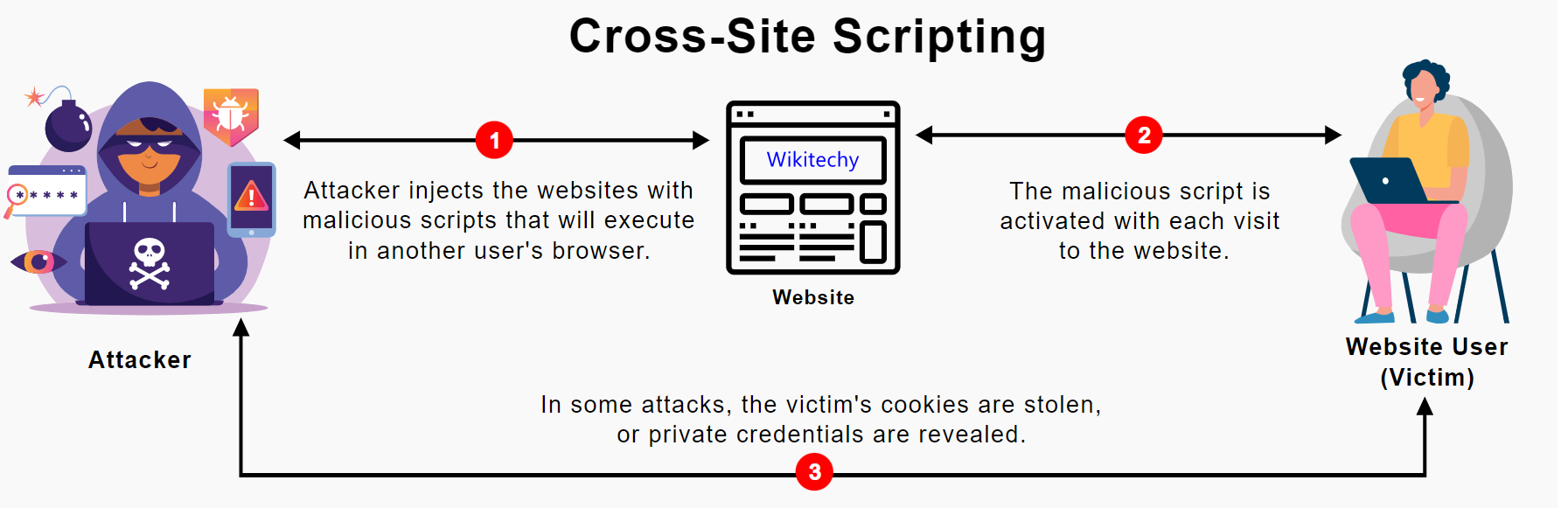
- In this type of attack, an attacker injects malicious codes into websites that are typically downloaded and displayed by a vulnerable browser.
- An attacker can use XSS to send a malicious script to an unsuspecting user.
- The end user’s browser has no way to know that the script should not be trusted, and will execute the script.
- Because it thinks the script came from a trusted source, the malicious script can access any cookies, session tokens, or other sensitive information retained by the browser and used with that site.
- Cross-site scripting (XSS) is a computer security vulnerability typically found in web applications that enable attackers to inject client-side script into web pages viewed by other users.
Session Fixation Attack
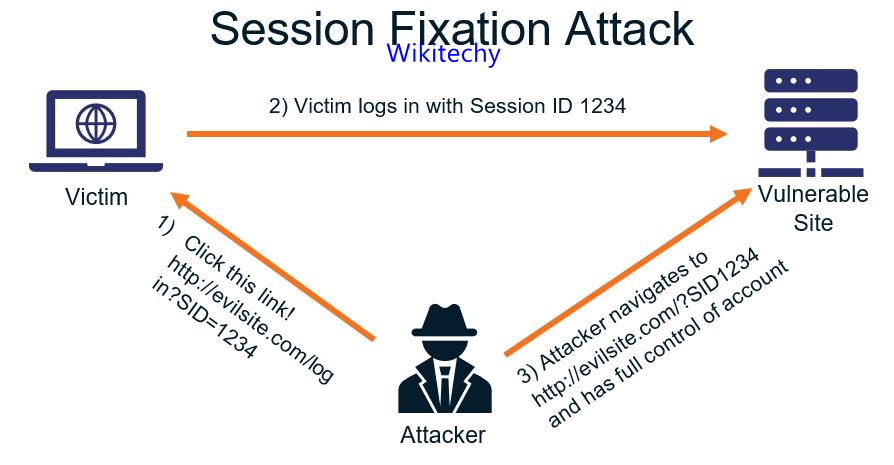
- A session fixation attack is a type of remote code execution attack which is used to exploit software designed with the web-server Session Management feature.
- When a website is running an HTTP server, the server’s session state information can be stolen and then retrieved by an attacker to take over the browser or use it for further attacks.
- There are many tools that can help you detect session fixation attacks in your organization in order to prevent future attacks.
- A Session fixation attack is also known as Session Fixation Vulnerability (SFV).
Detection
- The best way to mitigate client-side attacks is through system patching.
- System patching is the most basic and cost-effective method to lower the attack surface.
- It is important to keep up with patches and avoid vendor updates that patch vulnerabilities in software that are not relevant to the overall corporate environment.
- The best way to prevent client-side attacks is through a secure, strong password policy that dictates common passwords or patterns of many modern authentication technologies, including NTLM, MD4, DIGEST-MD5, and SHA1.
Countermeasures
Steps to take to prevent client-side attacks
- Install antivirus software, anti-spyware software, and firewall protection on all workstations, servers, and wireless devices.
- Ensure the latest system software patches are applied regularly.
- Maintain a complete backup system of all data on all systems use a separate server or external hard drive or network location to store backups that are no longer needed and keep them off the system they were created on.
- If a user is logging in from an unknown location or IP address, consider blocking access from those locations (access control lists).
- Prevent unauthorized access to accounts.
- Use strong passwords and avoid common passwords or patterns that can lead to vulnerabilities, like “Admin” or “12345”.
- Limit login attempts (user lockout).
