A denial-of-service (DoS) attack is a type of cyber-attack in which a malicious actor goals to render a computer or other device unavailable to its planned users by disturbing the device’s normal functioning. DoS attacks typically function by awesome or flooding a targeted machine with needs until normal traffic is unable to be processed, resultant in denial-of-service to additional users. A DoS attack is considered by using a single computer to launch the attack.
A distributed denial-of-service (DDoS) attack is a type of DoS attack that comes from many distributed sources, such as a botnet DDoS attack.

How does a DoS attack work ?
The main focus of a DoS attack is to oversaturate the volume of a targeted machine, resultant in denial-of-service to additional requests. The multiple attack vectors of DoS attacks can be grouped by their similarities.
DoS attacks typically fall into 2 categories:
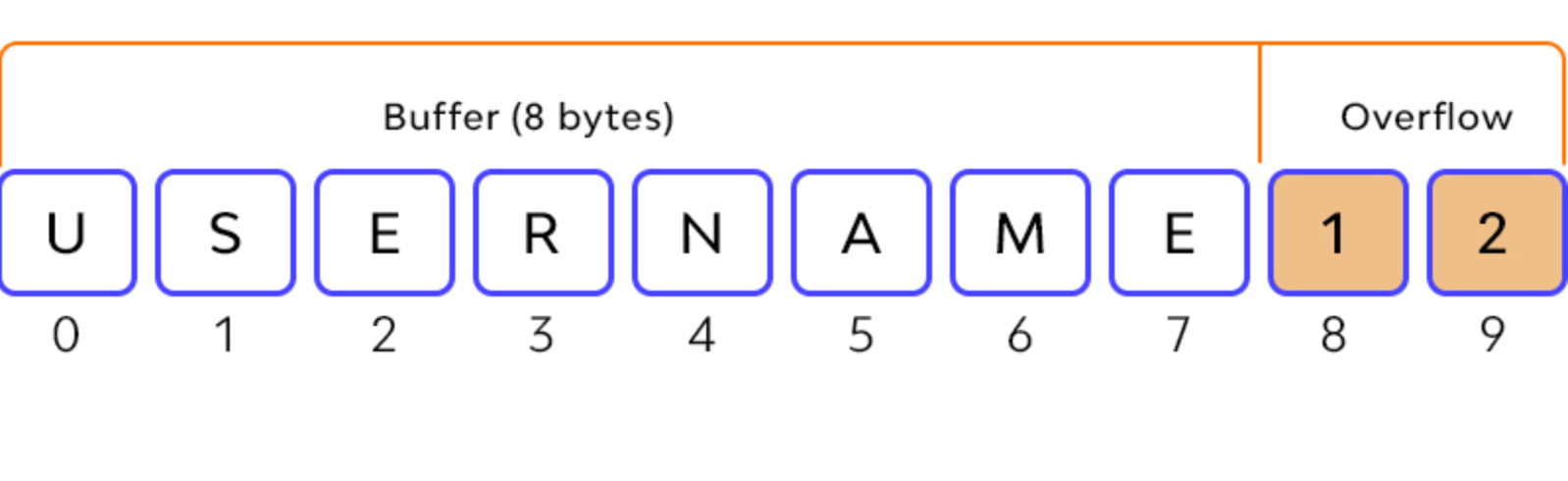
Buffer overflow attacks
- An attack type in which a memory buffer overflow can cause a machine to consume all available hard disk space, memory, or CPU time. This form of activity often results in slow behavior, system crashes, or other harmful server behaviors, resulting in denial-of-service.
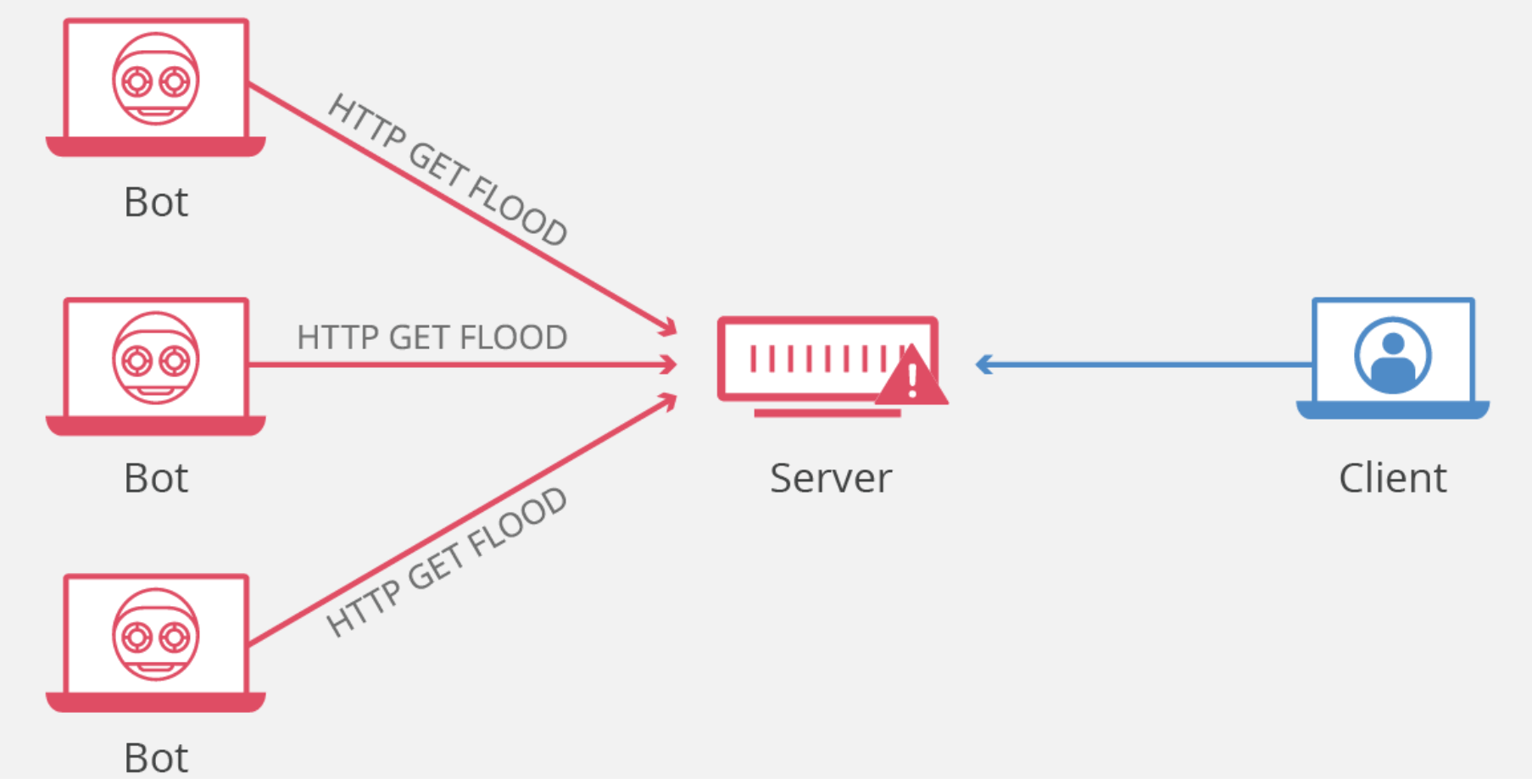
Flood attacks
- By saturating a targeted server with an overwhelming amount of packets, a malicious actor is able to oversaturate server capacity, resultant in denial-of-service. In order for most DoS flood attacks to be successful, the malicious actor must have more offered bandwidth than the target.
How can you tell if a computer is experiencing a DoS attack ?
It can be difficult to separate an attack from other network connectivity errors or heavy bandwidth consumption, some characteristics may indicate an attack is happening.
DoS attack indications include:
- A typically slow network performance such as long load times for files or websites.
- The failure to load a particular website such as your web property.
- A sudden loss of connectivity across devices on the same network.
How do you avoid being part of the problem ?
There is no way to fully avoid becoming a target of a DoS or DDoS attack, there are hands-on steps managers can take to reduce the effects of an attack on their network.
- Enroll in a DoS protection service that senses irregular traffic flows and redirects traffic away from your network. The DoS traffic is filtered out, and clean traffic is passed on to your network.
- Create a disaster recovery plan to confirm successful and efficient communication, mitigation, and recovery in the event of an attack.
It is also important to take steps to support the security posture of all of your internet-connected devices in order to stop them from being cooperated.
- Install and maintain antivirus software.
- Install a firewall and configure it to restrict traffic coming into and leaving your computer.
- Evaluate security settings and follow good security practices in order to minimize the access other people have to your information, as well as achieve unwanted traffic .