Sniffing is a process of capturing and monitoring all data packets passing through given network. Sniffers are used by system/network administrator to monitor and troubleshoot network traffic. Attackers use sniffers to capture data packets covering sensitive information such as password, account information etc. It can be hardware or software installed in the system. By placing a packet sniffer on a network in promiscuous mode, a malicious intruder can capture and analyze all of the network traffic.
Types of Sniffing
- Active Sniffing
- Passive Sniffing
Active Sniffing
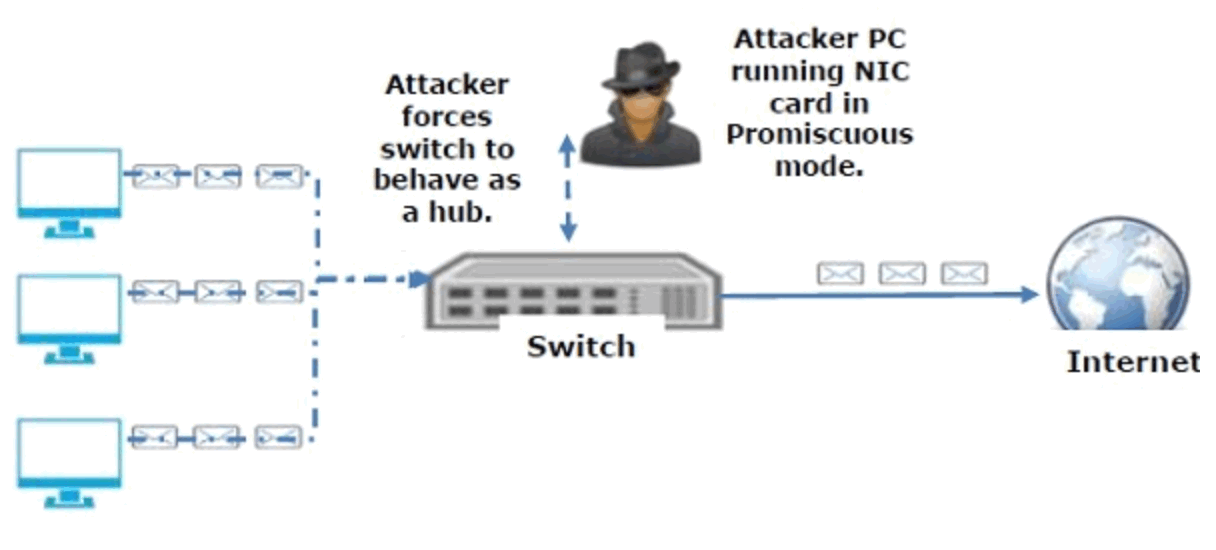
Sniffing in the switch is active sniffing. A switch is a point to point network device. The switch controls the flow of data between its ports by dynamically monitoring the MAC address on each port, which supports it pass data only to its planned target. In order to capture the traffic between target sniffers has to actively inject traffic into the LAN to allow sniffing of the traffic. This can be done in various ways.
Passive Sniffing
This is the process of sniffing via the hub. Any traffic that is passing through the non-switched or unbridged network segment can be seen by all machines on that segment. Sniffers work at the data link layer of the network. Any data sent across the LAN is really sent to each and every machine linked to the LAN. This is called passive since sniffers located by the attackers passively wait for the data to be sent and capture them.
What can be sniffed ?
One can sniff the following sensitive data from a network −
- Web traffics
- Telnet passwords
- Router configuration
- Chat sessions
- Email traffic
- FTP passwords
- DNS traffic
Ethical Hacking – Sniffing Tools
- BetterCAP
- It is a powerful, flexible and portable tool created to perform many types of MITM attacks against a network, manipulate HTTP, HTTPS and TCP traffic in real-time, sniff for credentials, and much more.
- Ettercap
- It is a complete suite for man-in-the-middle attacks. It features sniffing of live connections, content filtering on the fly and many other exciting tricks. It supports active and passive partition of many protocols and contains many features for network and host analysis.
- Wireshark
- It is used by packet sniffers. It offers a fabulous number of features designed to assist in the partition and analysis of traffic.
- Tcpdump
- It is a well-known command-line packet analyzer. It offers the ability to stop and see TCP/IP and other packets during transmission over the network.
- WinDump
- A Windows port of the popular Linux packet sniffer tcpdump, which is a command-line tool that is perfect for displaying header information.
- OmniPeek
- Manufactured by WildPackets, OmniPeek is a commercial product that is the evolution of the product EtherPeek.
- Dsniff
- A suite of tools planned to perform sniffing with different protocols with the intent of intercepting and revealing passwords. Dsniff is designed for Unix and Linux platforms and does not have a full equivalent on the Windows platform.
- EtherApe
- It is a Linux/Unix tool considered to display graphically a system’s incoming and outgoing connections.
- MSN Sniffer
- It is a sniffing utility definitely designed for sniffing traffic created by the MSN Messenger application.
- NetWitness NextGen
- It contains a hardware-based sniffer, along with other features, designed to monitor and analyze all traffic on a network. This tool is used by the FBI and other law enforcement agencies.
How to protect your system from a sniffer
- Use strong antivirus software :
- Antivirus will stop malware from invading your system. It will also detect anything that shouldn’t be on your computer — like a sniffer — and help you delete it.
- Use a VPN:
- A Virtual Private Network encrypts your connection and hides all the data sent from your computer over the internet. That means that a sniffer spying on your traffic would just see scrambled info, and your data stays safe.
- Avoid insecure protocols:
- To make sure that your data stays protected while you’re out there surfing the wide web is to check for HTTPS. When you look at the address bar of a website you’ll either see HTTP or HTTPS. Some browsers will show a lock symbol to indicate HTTPS. Only HTTPS is secure, meaning that your public services are encrypted. HTTP is insecure, and your browser may show a little i instead of the lock symbol. You should avoid HTTP when possible, and specially do so when shopping online.
- Watch out for social engineering:
- Cybercriminals use methods like phishing emails and infected websites to trick victims into innocently downloading sniffers. Training smart browsing tactics and common sense to avoid everything fishy.