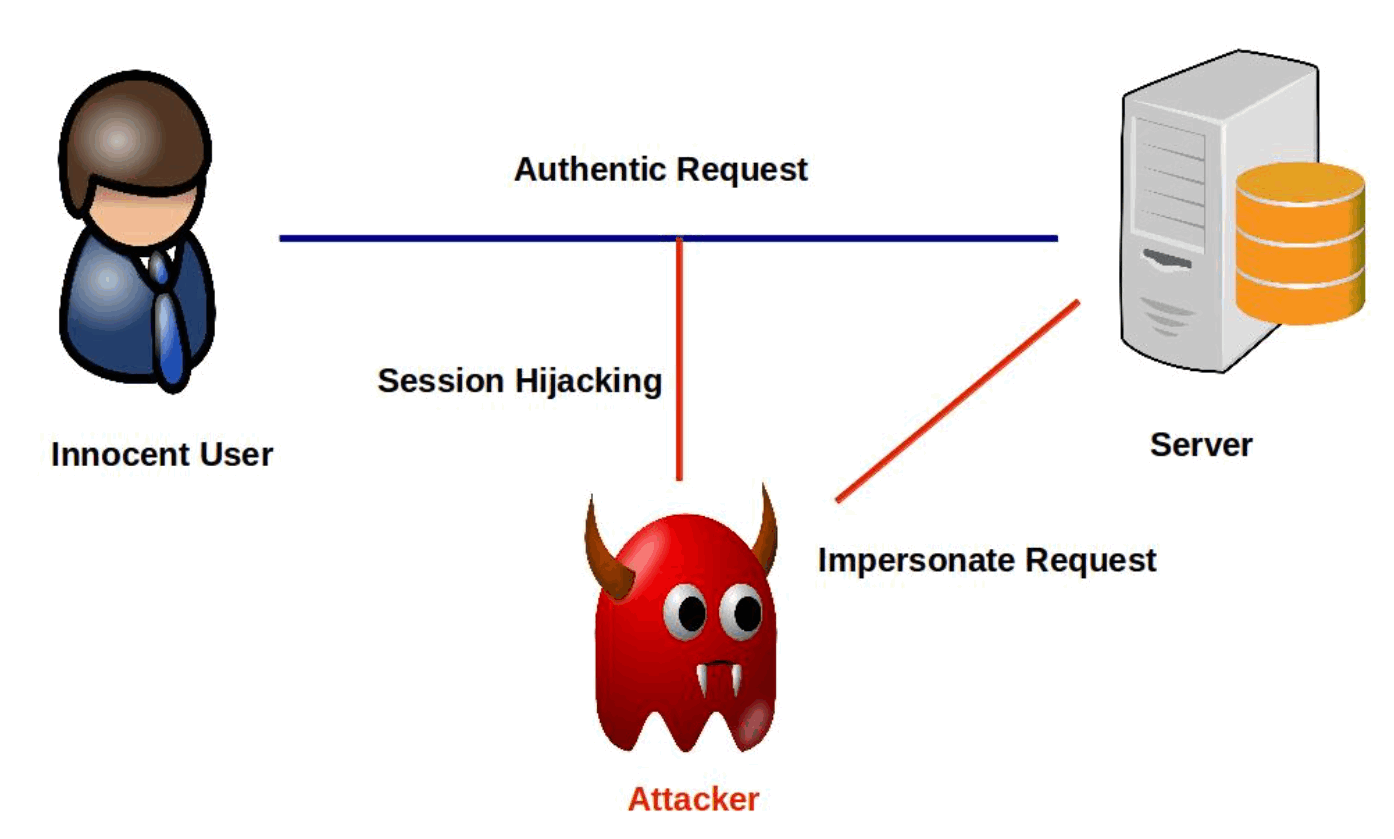
It is defined as taking over an active TCP/IP communication session without the user’s permission. When executed successfully, attackers undertake the uniqueness of the compromised user, liking the same access to resources as the compromised user. Identity theft, Information theft, thieving sensitive data are common effects of session hijacking.
Types of session hijacking attacks:
- Active Hijacking
- Passive Hijacking
Active Hijacking :
The attacker will calm one of the machines, generally the client computer, and take over the users’ position in the communication exchange between the workplace and the server. The active attack also permits the attacker to issue instructions on the network making it possible to create new user accounts on the network, which can later be used to gain access to the network without having to achieve the session hijack attack.
Passive Hijacking :
Here the attacker monitors the traffic between the workstation and server. The main goal for the passive attack is to monitor network traffic and potentially determine valuable data or passwords.
Session Hijacking Process
The initial step in the session hijack attack is locating a target user. Attackers look for two things prior to their attack- first, they look for networks that have a high level of operation; high volume networks help attackers to remain unnamed and they also provide a well supply of users to choose from, which also helps the attack. Secondly, users who use insecure network protocols such as Telnet , rlogin (remote login), and FTP (file transfer protocol) are easy goals due to their integrally insecure design. Packet sniffing software can be used to sniff network traffic for the purpose of locating vulnerable protocols like FTP, Telnet, and rlogin. Port scanning software can also be used to find servers that have FTP, Telnet, or rlogin ports open.
1. Sniffing into Active Session:
- The attacker then finds an active session among the target and another machine and places himself between them. Using a sniffer like Wireshark, he arrests the traffic and tries to collect information about the session.
2. Monitor:
- Here monitors the traffic for vulnerable protocols like HTTP, telnet, rlogin, etc., and efforts to find any valid authentication packets passing through.
3. Session Id Retrieval:
- The attacker tries to guess the session id using available information. Now that a target has been chosen, the next step in the session hijacking process is sequence number prediction.
- Sequence number prediction is a dangerous step because failing to predict the correct sequence number will result in the server sending reset packets and terminating the connection attempt.
- If the attacker guesses the sequence numbers wrong repeatedly, the chance of detecting the attack increases.
4. Stealing:
- In application-level hijacking, active attacks are followed to steal the session Id. Man in the middle attack, cross-site scripting, sniffing are used to steal the session id.
Brute Forcing: This is a time-consuming process.
- While sequencing number guessing can be done physically by skilled attackers, software tools are available to automate the process.
5. Take One of the Parties Offline:
- Once a session is chosen and sequence numbers predicted, one of the targets has to be silenced. This is usually done with a denial of service attack.
- The attacker make sure that the client computer remains offline for the duration of the attack, or the client computer will start transmitting data on the network causing the workstation and the server to frequently attempt to coordinate their connections; resultant in a condition known as an ACK storm.
6. Take over the Session and Maintain the Connection:
- The final phase of the session hijack attack involves taking over the communication session between the workstation and server.
- The attacker will spoof their client IP address, to avoid detection, and include a sequence number that was projected earlier. If the server accepts this information, the attacker has successfully attacked the communication session.